How to Prevent Expensive Cloud Routing Surprises With Proactive Intent Verification
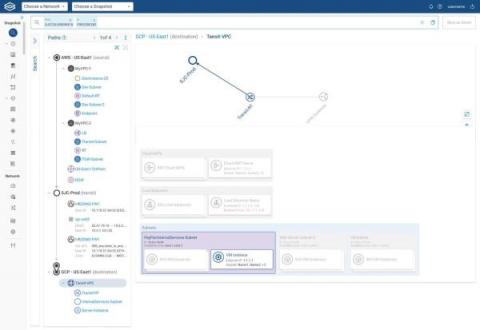
A six-figure surprise is awesome when it’s a lottery win. It’s not so awesome when it’s the “Amount Due” appearing in your monthly cloud bill. But enterprises receive these “surprises” all the time, and what can sting even more is trying to explain this preventable expense to management. Inefficient (not optimized) traffic routing to and from your various cloud instances and other services can hurt your business in other ways too.