Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
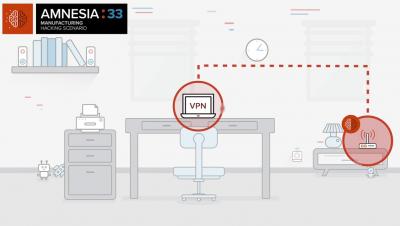
What is AMNESIA:33?
How to identify and mitigate risk from AMNESIA:33 vulnerabilities
The Year of the Pandemic and 2021 Cybersecurity Predictions
2020 will always be remembered as the year our lives changed dramatically due to the Coivd-19 pandemic. Here our panel of security experts look back at the lessons learned in the past 12 months and share their predictions for the key security challenges organizations will face in 2021.
Six key findings from the 'DevSecOps Practices and Open Source Management in 2020' report
This week Synopsys released the “DevSecOps Practices and Open Source Management in 2020” report, findings from a survey of 1,500 IT professionals working in cyber security, software development, software engineering, and web development. The report explores the strategies that organizations around the world are using to address open source vulnerability management, as well as the problem of outdated or abandoned open source components in commercial code.
4 Things a Good Vulnerability Management Policy Should Include
Organizations face an ever-evolving threat landscape. With this in mind, it is imperative that organizations keep an up-to-date vulnerability management policy for remediating and controlling security vulnerabilities that may lead to a breach. A good vulnerability management policy should contain the following.
Detectify checks for critical Oracle WebLogic Server RCEs (CVE-2020-14882, CVE-2020-14750)
On October 29th, Detectify released a security test to detect a critical Oracle WebLogic Server RCE – CVE-2020-14882. Again in November, Oracle released an out-of-band security patch to fix a related RCE for Oracle Fusion Middleware. These vulnerabilities are currently being exploited by multiple botnets in the wild. Detectify scans your application for both of these vulnerabilities and will alert you if you are running a vulnerable version of Oracle WebLogic Server.
How to mitigate Ransomware attacks
Ransomware is a serious security threat affecting companies of all sizes and industries. While the symptoms (an attack) can be extremely damaging and disruptive, the solution can be simple - proactive prevention through a heavy dose of security hygiene. Here we cover the basics of Ransomware and top tips for securing your organization against it.
Four requirements for open source vulnerability management in a DevOps environment
Most applications contain open source code, which can expose companies to risks if left unchecked. Make the most of your open source vulnerability management with the right approach and tooling.