What is Ransomware?
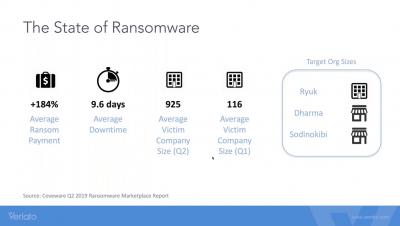
Ransomware is a type of malicious software, or malware, designed to deny access to a computer system or data until ransom is paid. Ransomware spreads through phishing emails, malvertising, visiting infected websites or by exploiting vulnerabilities. Ransomware attacks cause downtime, data leaks, intellectual property theft and data breaches. Ransom payment amounts range from a few hundred to hundreds of thousands of dollars. Payable in cryptocurrencies like Bitcoin.