Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Monitoring
Practical CPU time performance tuning for security software: Part 1
Software performance issues come in all shapes and sizes. Therefore, performance tuning includes many aspects and subareas, and has to adopt a broad range of methodologies and techniques. Despite all this, time is one of the most critical measurements of software performance. In this multi-part series, I’ll focus on a few of the time-related aspects of software performance — particularly for security software.
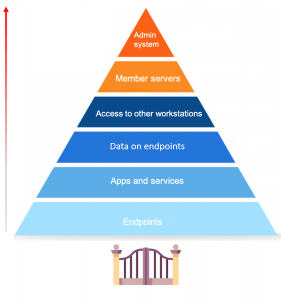
The role of endpoints in the security of your network
Endpoint security is a hot topic of discussion, especially now with so many businesses shifting to remote work. First, let’s define what endpoints are. Endpoints are end-user devices like desktops, laptops, and mobile devices. They serve as points of access to an enterprise network and create points of entry that function as gateways for malicious actors. Since end-user workstations make up a huge portion of endpoints, we’ll be focusing on their security.
Introducing New Cloud Security Monitoring & Analytics Apps
The Payments Canada SUMMIT: Making the Vision of Modernization a Reality
A couple of weeks ago The Payments Canada SUMMIT gathered more than 2,000 delegates from financial institutions in Canada and around the world for a virtual one-week conference. INETCO was a sponsor of Canada’s premier payments event. Our team participated in industry discussions, met peers, and learned more about future innovation opportunities in the financial ecosystem. 2021 was a record-breaking year for The Payments Canada SUMMIT.
Automate remediation of threats detected by Datadog Security Monitoring
When it comes to security threats, a few minutes additional response time can make the difference between a minor nuisance and a major problem. Datadog Security Monitoring enables you to easily triage and alert on threats as they occur. In this post, we’ll look at how you can use Datadog’s webhooks integration to automate responses to common threats Datadog might detect across your environments.
ISS GEO Tracking with Graylog
Graylog and Sysmon
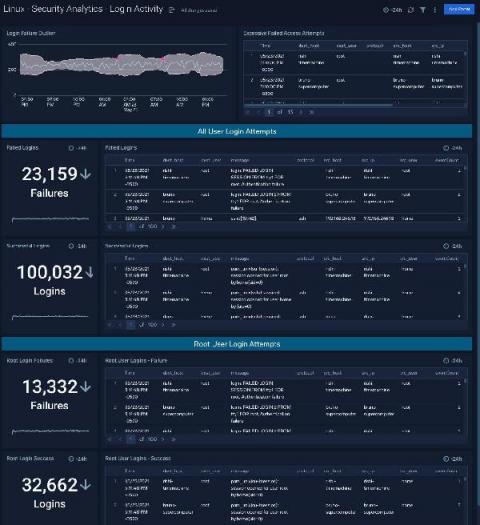
How South Dakota Bureau of Information and Telecommunications deploys Elastic to secure endpoints
The South Dakota Bureau of Information and Telecommunications (BIT) provides quality customer services and partnerships to ensure South Dakota’s IT organization is responsive, reliable, and well-aligned to support the state government’s business needs. The BIT believes that “People should be online, not waiting in line.” The bureau’s goals for the state's 885,000 residents include.