Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Monitoring
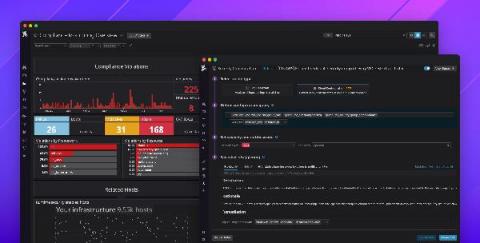
Introducing Datadog Cloud Security Posture Management
Governance, risk, and compliance (GRC) are major inhibitors for organizations moving to the cloud—and for good reason. Cloud environments are complex, and even a single misconfigured security group can result in a serious data breach. In fact, misconfigurations were the leading cause of cloud security breaches in 2020. This puts a lot of pressure on developer and operations teams to properly secure their services and maintain regulatory compliance.
Practical CPU time performance tuning for security software: Part 2
In a previous blog, we discussed how to monitor, troubleshoot, and fix high %CPU issues. We also revealed a system API that could have an unexpected impact on CPU consumption. In this episode, we’ll discuss another time-related performance aspect that is unique to security software: application startup time. You don’t need to be a developer to benefit from this article.
How to Prevent Man-In-The-Middle Attacks and Fight Financial Fraud
You just started reading this blog post. But are you reading it alone? Or is there a “man in the middle” watching and recording everything you do online? While it may sound like a plot from a Hollywood blockbuster, the reality is far from amusing. A man-in-the-middle (MitM) attack can quickly occur when an unsuspecting victim joins the same public Wi-Fi network as a malicious attacker, for example, at a cafe.
Ingesting threat data with the Threat Intel Filebeat module
The ability for security teams to integrate threat data into their operations substantially helps their organization identify potentially malicious endpoint and network events using indicators identified by other threat research teams. In this blog, we’ll cover how to ingest threat data with the Threat Intel Filebeat module. In future blog posts, we'll cover enriching threat data with the Threat ECS fieldset and operationalizing threat data with Elastic Security.
6 Ways to Support a Remote DevOps Team
Search and Dashboards
Why companies need URL filtering for enhanced cloud protection
The cloud landscape is rife with unsafe URLs and inappropriate content. This—coupled with the accelerated adoption of cloud applications in the workplace—has created an urgent need to scrutinize and control the use of these online resources to prevent data theft, exposure, and loss. This blog elaborates on how a robust URL filtering solution can help manage what cloud services your employees use and how they interact with these services.
EventSentry on GitHub: PowerShell module, templates and more!
Since we’ve accumulated a lot of resources around EventSentry that are updated frequently, we’ve decided to launch a GitHub page where anyone can access and download scripts, configuration templates, screen backgrounds and our brand-new PowerShell module that is still under development.