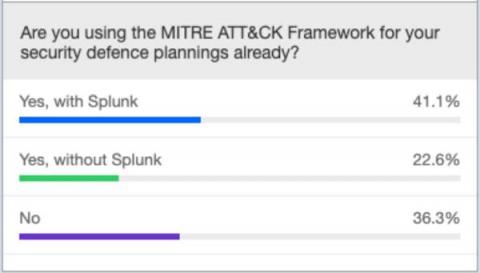
In Cybersecurity, AI is Not A-OK
Artificial intelligence has been (and continues to be) a popular topic of discussion in areas ranging from science fiction to cybersecurity. But as much fun as it might be to discuss my favorite sci-fi AI stories, let’s set aside the works of Asimov, Bradbury and other storytellers to focus on the role of AI in cybersecurity.