Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
Open Policy Agent: The Top 5 Kubernetes Admission Control Policies
Kubernetes developers and platform engineers are typically under a metric ton of pressure to keep app deployments humming at a brisk pace. With the scale and power of Kubernetes, this can feel daunting. Maybe you’re a retailer launching a new e-commerce feature for a huge sale. Maybe you’re a bank that’s scaling a finance app worldwide. In either case, compromises always get made in the interest of speed and schedules.
Securing AWS Fargate workloads: Meeting File Integrity Monitoring (FIM) requirements
Securing AWS Fargate serverless workloads can be tricky as AWS does not provide much detail about the internal workings. After all… it’s not your business, AWS manages the scaling of underlying resources for you. :) While the security and stability of Fargate’s system is an inherent feature, Fargate follows a shared responsibility model, where you still have to take care of securing those parts specific to your application..
AWS Fargate runtime security - Implementing File Integrity Monitoring with Sysdig
What Docker runtime deprecation means for your Kubernetes
On December 8, 2020, Kubernetes released version 1.20—the third and final release of the popular container orchestration platform in 2020. Kubernetes noted in a blog post that the version contained 42 enhancements. Of those enhancements, 16 entered into alpha, while the remainder moved to beta or graduated to stable at 15 and 11, respectively.
Exploiting and detecting CVE-2021-25735: Kubernetes validating admission webhook bypass
The CVE-2021-25735 medium-level vulnerability has been found in Kubernetes kube-apiserver that could bypass a Validating Admission Webhook and allow unauthorised node updates. The kube-apiserver affected are: You are only affected by this vulnerability if both of the following conditions are valid: By exploiting the vulnerability, adversaries could bypass the Validating Admission Webhook checks and allow update actions on Kubernetes nodes.
Our $188M funding round fuels our mission to help customers confidently run modern cloud applications
Today, I am excited to share that we secured $188M in a new funding round, at a valuation of $1.19B (read more here). At the outset, I want to thank our employees, partners, investors and most importantly, our customers for this important milestone. The funding follows a year of unmatched innovation that led to accelerated revenue growth, installed base growth, and rapid community adoption of our open source projects.
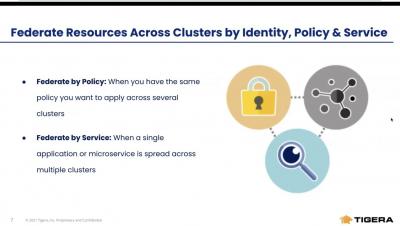
Why We Need to Rethink Authorization for Cloud Native
Companies have moved to cloud native software development so that they can increase development speed, improve product personalization, and differentiate their buyer experiences in order to innovate and win more customers. In doing so, enterprises have also redefined how they build and run software at a fundamental level.