What is an Information Security Policy?
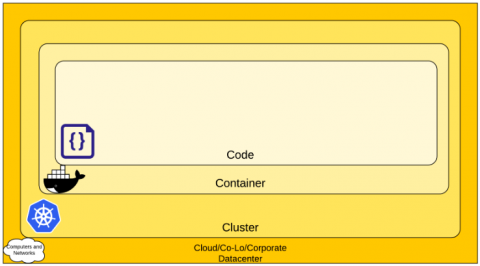
An information security policy (ISP) is a set of rules, policies and procedures designed to ensure all users and networks within an organization meet minimum IT security and data protection security requirements. ISPs should address all data, programs, systems, facilities, infrastructure, users, third-parties and fourth-parties of an organization.