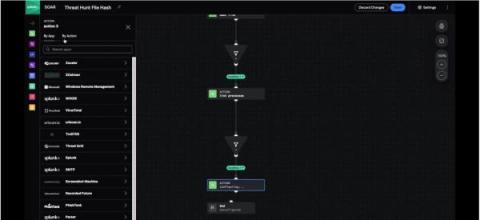
Monitoring Networks with Snort IDS-IPS
Networks are the data highways upon which you build your digital transformation infrastructure. Like interstate highways transmit goods, networks transmit data. Every connected user and device is a network digital on-ramp. When malicious actors gain unauthorized access to networks, organizations must detect and contain them as quickly as possible, requiring security analysts to embark on a digital high-speed chase.