IoT Monitoring: Protecting & Maintaining IoT Devices in 2023
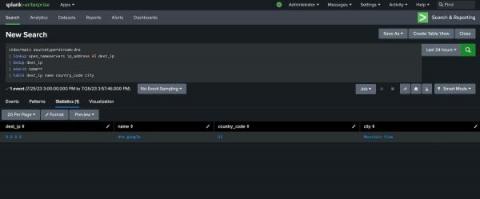
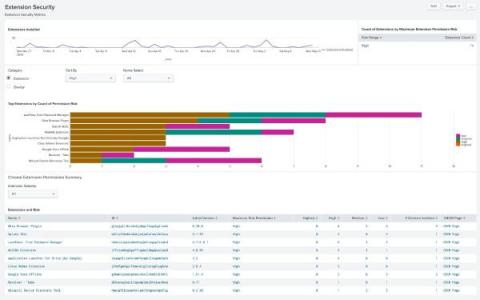
The state of cybersecurity is in constant flux — meaning we must constantly iterate and revisit our systems to protect ourselves. With security logging and monitoring failures moving up to number 9 of the OWASP Top 10, organizations everywhere are revisiting their stance on network and application monitoring. This is great for getting a pulse check on security posture and is certainly key in any good strategy, but we might be forgetting something — IoT devices.