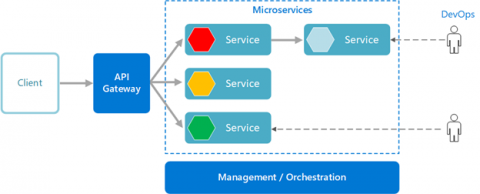
As the complexity and sophistication of cybersecurity threats increase, businesses across all sectors are seeking effective solutions to protect their critical data and digital infrastructures. One emerging solution is Extended Detection and Response (XDR), an integrated suite of security products that collectively provide preventive, detective, and responsive capabilities. As organisations in the UK increasingly consider this approach, let's delve into the best practices for implementing managed XDR services.