Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Microservices
Why You Need Continuous Monitoring in Microservices
The microservices architecture is a software development strategy in which applications are broken down into smaller components called microservices. Each microservice is responsible for a specific task or business function and communicates with other microservices through application programming interfaces (APIs). Effectively managing a microservices application requires monitoring, much like any other IT infrastructure.
Navigating the Evolution: A Tactical Guide to Monolithic to Microservices Transformation
How to Secure Communication Between Microservices
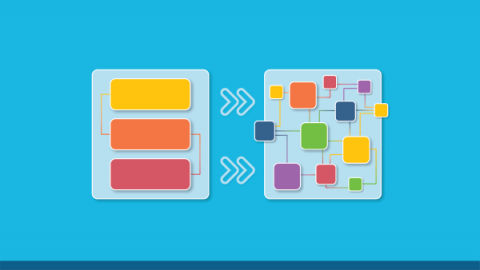
The migration to microservice architecture from monolithic applications is happening en masse as enterprises realize its scalability and efficiency benefits. According to an IBM report1, 56% of nonuser organizations plan on adopting the microservice architecture by 2023. Breaking an application into small, loosely coupled services lets independent teams quickly design and deploy these components.
What is Service-to-Service Authorization?
A microservice application comprises small autonomous services that communicate with each other through application programming interfaces (APIs) — as standalone services or via a service mesh. These API calls or requests raise security and compliance concerns if not appropriately secured through authentication and authorization checks. Service-to-service authorization is the process of determining what actions an authenticated service is allowed to perform based on pre-defined policies.
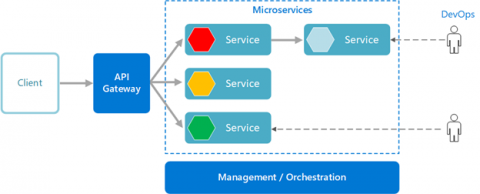
What is Service Mesh in Microservices?
The microservice architecture involves breaking the application into small interconnected services, each performing a specific task. This breakdown enables developers to work on individual services without affecting the rest of the application, leading to more agility and easier scaling. These services communicate through APIs and, as the number of services within an application increases, developers may introduce a microservice service mesh to control all the service-to-service communication.
How to improve your microservices architecture security
Microservices Security: Fundamentals and Best Practices
The many benefits of microservices architecture, such as improved scalability and agility, explain why organizations are migrating from the traditional monolithic architecture. However, these benefits come at the cost of increased complexity, especially regarding security. According to an O’Reilly survey, 56% of respondents considered increased complexity the greatest challenge in developing microservices.
Security Challenges in Microservices
Before the rise of cloud computing and small autonomous services built with containers, a typical application would consist of a monolith of code with a frontend, a backend and a database. Developers would take extra caution when updating their code because any change or bug could affect the entire application. As an alternative, microservices broke down applications into small interconnected services — each responsible for their discrete function, collaborating using APIs.
How to Enforce Fine-Grained Authorization in Microservices
The shift from monolithic architectures to microservices poses complex authorization challenges to development teams. In this article, we look at how to enforce fine-grained access control in cloud-native environments as we make a case for a dynamic approach to authorization in microservices. Key takeaways.