Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Software Deployment Tools: SCCM vs Intune vs GPO vs More
There are many software deployment tools to deliver software and updates to your endpoints, but just because you have a lot of options doesn’t mean it has to be confusing. You might pick one software deployment tool to do it all, or you might pick several automated software deployment tools depending on your needs.
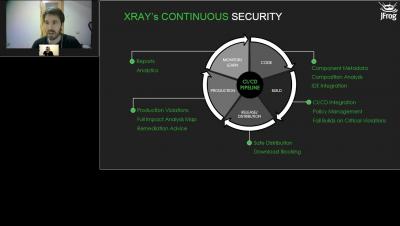
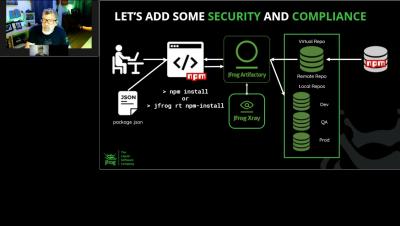
Episode 1: DevSecOps Coffee Break Series Add OSS Security & Compliance to Artifactory
Episode 2: DevSecOps Coffee Break Series | Creation of Your Software Bill Of Materials SBOM
Episode 4: DevSecOps Coffee Break Series | 'Shift Left' Security With A Developer Centric Approach
Episode 5: DevSecOps Coffee Break Series | If JFrog is Good Enough For The Government, Why Not You
Episode 3: DevSecOps Coffee Break Series | Securing Your Software Supply Chain
LimaCharlie & Atomic Red Team Enable a DevOps Approach to Cybersecurity
Engineering is both an art and a science. It requires creative thinking but is bounded by a rigidity which enables measurement and progress. We can only see so far because we stand on the shoulders of giants… and because those giants kept really good notes. Cybersecurity is growing up and it has to. Cyber is no longer the domain of shadowy figures in hoodie sweatshirts, it now has a presence in the C-suite.
Java JSON deserialization problems with the Jackson ObjectMapper
In a previous blog post, we took a look at Java’s custom serialization platform and what the security implications are. And more recently, I wrote about how improvements in Java 17 can help you prevent insecure deserialization. However, nowadays, people aren’t as dependent on Java’s custom serialization, opting instead to use JSON. JSON is the most widespread format for data serialization, it is human readable and not specific to Java.
How to Pass a FedRAMP Audit for SaaS Providers: Part 1
You work at a SaaS provider, and now you need to pass a FedRAMP audit. If that describes you, read on. This post will tell you (almost) everything you need to know about how to pass a FedRAMP Audit. For the rest, reach out to us. We will put you in touch with one of our Solution Engineers like me who have helped some of the largest SaaS providers in the world pass their FedRAMP audit prior or after IPOing. It’s what we do.