Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
Things You Must Know About Cyber Security in the Cloud
How to protect Node.js apps from CSRF attacks
A cross-site request forgery attack (CSRF) attack is a security vulnerability capitalizing on trust between a web browser and a legitimate website. Crafty attackers manipulate browsers into executing malicious actions on websites where users authenticate themselves and log in. Often, these attacks start when users click a link attached to a deceptive email or land on a compromised website, unaware of the logic executing in the background.
Cisco issues warning for critical 0-day vulnerability exploited in the wild
Cisco has issued a warning regarding a critical security vulnerability (CVE-2023-20198) affecting its IOS XE software. With a severity rating of 10.0 on the CVSS scoring system, the vulnerability grants remote attackers full administrator privileges on affected devices without authentication.
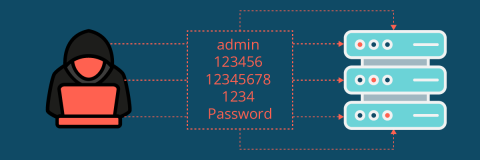
IT admins are just as culpable for weak password use
New data from Outpost24 reveals that IT administrators could be just as predictable as end-users when it comes to passwords. An analysis of just over 1.8 million passwords ranks ‘admin’ as the most popular password with over 40,000 entries, with additional findings pointing to a continued acceptance of default passwords.
HTTP/2 Rapid Reset Attack Vulnerability
Cisco iOS XE Vulnerability: CVE-2023-20198
Cisco has released an advisory, acknowledging active exploitation of a previously unknown vulnerability, which is tracked as CVE-2023-20198, in the web UI feature of Cisco IOS XE Software when exposed to the internet or to untrusted networks. This vulnerability allows a remote, unauthenticated attacker to create an account on an affected system with privilege level 15 access, which is the highest level of access.
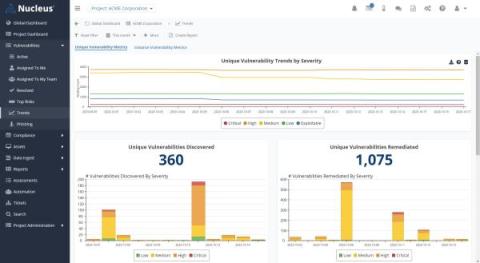
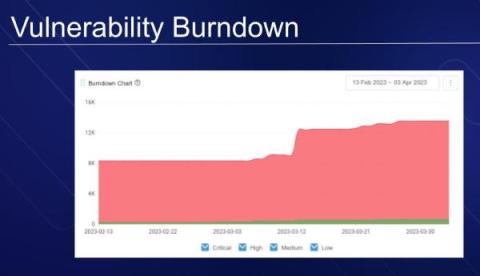
Get Management Buy-in with AppSec Metrics
Getting management to back your application security plans can be a tough sell. Metrics are vital because they help you understand how effective your initial cybersecurity measures are and how to turn them into measurable data that's easy for everyone to understand. This article will explore how to use metrics to get the support you need and make your application security programs more effective.
Navigating the Unknown: Zero-Days in the Supply Chain
Zero-days are out there. Lurking just under the surface, waiting for the right moment to strike. A security team can do everything right and still experience a zero-day attack in its supply chain. And with innumerable configurations, devices, and platforms that can be exploited, zero-day exploits are becoming more common than ever.