Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
4. SWAT Onboarding - Outpost24 SWAT Recreation Flow and Explanation
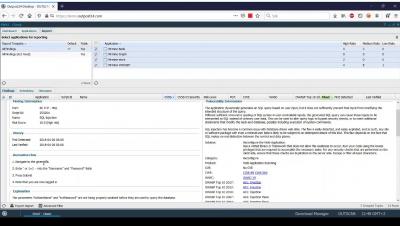
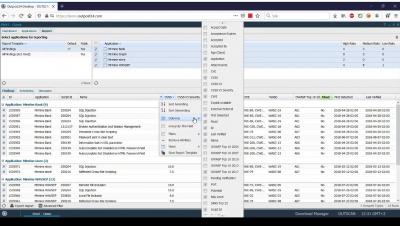
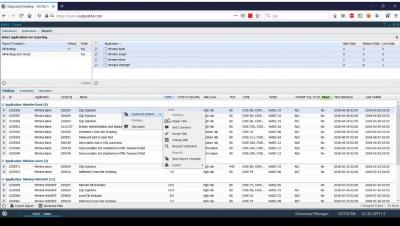
3. SWAT Onboarding - Reporting and Filtering
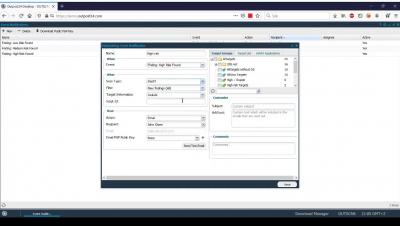
1. SWAT Onboarding - Event Notification
5. SWAT Onboarding - Discussion and Verification with Our Security Experts
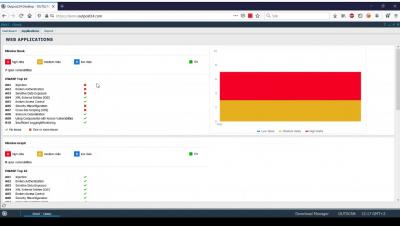
2. SWAT Onboarding - Application Overview
The top 10 most-targeted security vulnerabilities - despite patches having been available for years
Newly-discovered zero-day vulnerabilities may generate the biggest headlines in the security press, but that doesn’t mean that they’re necessarily the thing that will get your company hacked. This week, US-CERT has published its list of what it describes as the “Top 10 Routinely Exploited Vulnerabilities” for the last three years.
The 4 Stages to a Successful Vulnerability Management Program
Have you ever been around someone who is just better at something than you are? Like when you were in school and there was this person who was effortless at doing things correctly? They had great study habits, they arrived on time, they were prepared and confident in the materials that they studied in class, and they were a consistently high performer at every stage?
May Open Source Security Vulnerabilities Snapshot
May is here, and with it our May’s open source security snapshot, our monthly overview of the new open source security vulnerabilities published in April, to see what’s new in the ever-evolving open source security ecosystem. In order to give you all the low-down on emerging or ongoing trends, our hardworking research team analyzed all of the new open source security vulnerabilities added to the WhiteSource database.