Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
opsdemon
Latest posts
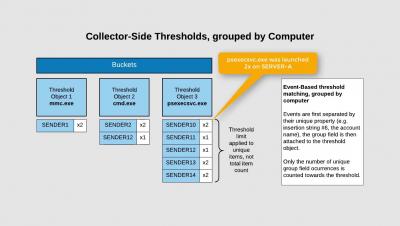
Detecting Lateral Network Movement / Spread in EventSentry
How to detect lateral movement on a network in real time with EventSentry, based on the example of a process spreading.
Securing Exchange Server OWA & ActiveSync - Proactive Security with EventSentry
With the proper auditing enabled (Logon/Logoff – Logon (Failure)) and EventSentry installed however, we can permanently block remote users / hosts who attempt to log on too many times with a wrong password. Setting this up is surprisingly simple.
Seven Unforgivable Sins of Sometime Security Providers
Traditional security providers lack capabilities to address today's critical use cases. This eBook discusses seven of these gaps and how you can address them.
Network Administrator's Guide to DevOps
The transformation of physical networks and infrastructure into easier-to-manage virtualized/software components, hybridization of IT operations and software development roles, and the despecialization of job duties, among others, means that traditional networking roles- and arguably any IT roles with job titles ending with "admin"- will invariably disappear.
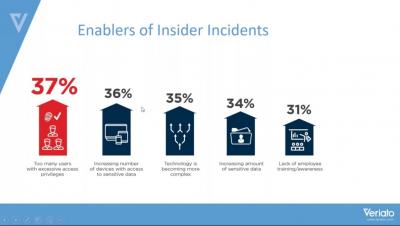
Effective Incident Response Through User Activity Monitoring
With the cost of a data breach eclipsing the $4 million mark, organizations need to pay close attention to any suspected cyber incident.
Egnyte in Media: Buzzfeed
BuzzFeed Safeguards Exclusive News and Journalistic Sources with Egnyte Protect.
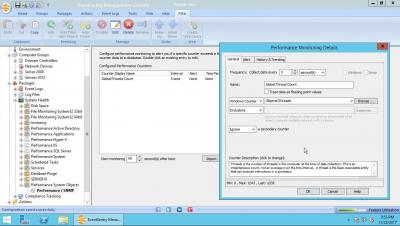
Monitoring Windows Performance Counters
How to monitor a Windows performance counter as well as create your own dynamic counter by combining two performance counters.
Design Within Reach - Egnyte in Retail
Design Within Reach Re-Invents Its Digital Workplace and improves employee productivity with Egnyte Connect and Google's G-Suite.
Egnyte Protect - Overview
Keeping your content secure is essential to maintaining a competitive edge and ensuring the privacy of your employees and customers. The key is to know who has access to what type of content, as well as where your sensitive content resides. We’ll show you how easy it can be.
Egnyte GDPR Compliance Solution
The key to GDPR accountability is forming an organized and transparent data plan. And that’s where we come in. Egnyte provides businesses with fast, adaptable and comprehensive support for GDPR compliance. Fast in that we’re up and running almost instantly, without hardware upgrades or software maintenance. Adaptable thanks to our European data center supporting businesses facing data residency restrictions. And comprehensive in that we’re the only service able to classify personal data from all 28 EU countries.