Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
opsdemon
Latest posts
Financial Data and Analysis Predictions for 2019
The use of big data and data from the internet of things (IoT) is changing business so rapidly it is hard to predict what is next, and financial analytics are certainly no exception. While the need for financial analysts continues to rise, the way analysts performs their day-to-day functions is evolving.
Third-Party Credentials and Vendor Risk: Safeguard Your Applications
Your primary systems aren’t the only source of damaging exposed credentials. Third-party applications employed by your organization also have privileged logins that must be protected. Cloud platforms, software as a service (SaaS), and local third party applications such as ERP systems often have administrative logins with full control.
Vendor Risk: The Impact Of Data Breaches By Your Third-Party Vendors
UpGuard’s researchers regularly uncover and report on corporate data breaches. We often find that the breach is not directly caused by the company, but by one of their third-party vendors. This series of posts is about a less-understood aspect of vendor risk, data breaches by third-party vendors. We will run you through many types of data breaches, how they relate to your third-party vendors, and ultimately what you can do to prevent them from hurting your business.
Big Data is Big Business: A Growing Trend of User Data Abuse and How to Protect Yourself
May 25, 2018 was the deadline for GDPR compliance. The media was abuzz. Businesses were rushing to update their privacy policy page. Companies were emailing newsletter subscribers to approve updated privacy policies. Everybody seemed to be paying attention to this new law, which appeared to be the beginning of a new dawn in data privacy. Or was it?
Machine Data: The True North in Digital Transformation
Pundits have been talking about ‘digital transformation’ since at least 1999, but it is a difficult concept to pin down, much less execute. Yet in a business environment in which former market leaders like Sears and GE are failing the challenge, the need for transformation has never been so stark.
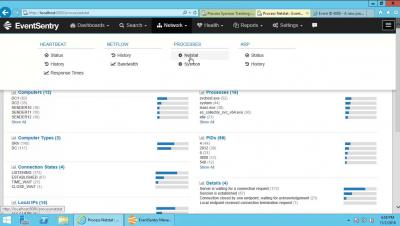
Process & Netstat Monitoring with EventSentry
Weekly Cyber Security News 02/11/2018
A selection of this week’s more interesting vulnerability disclosures and cyber security news. Another week of quite astounding news, and I will lead with a really interesting story from a side where many of us don’t get to tread (perhaps thankfully), though his closing question is very disconcerting…
Election Interference Attacks More than Voting Machines
When election interference is discussed, you probably think of “fake news” social media plots or hacked voting machines that manipulated outcomes. The truth is much more complicated. Election interference can come in many forms and have consequences that last long after an election cycle. Fortunately there are security measures elected officials, campaigns, and anyone with access to voter information can – and should – take to defend against election interference.
Cybersecurity & Formula 1 Racing - It's a Profession
Formula 1 is a serious business. It takes years of expertise and practical foot work to design, build and operate a winning Formula 1 team. It's easy to think that success depends on the car and the technology. But in reality, a cutting edge engine in the best car in the world can’t win a race alone. Without an expert driver and a highly experienced and dedicated support team, you just can’t finish first.