Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
opsdemon
Latest posts
Compliance Management Best Practices: When Will Excel Crush You?
The Insider's Guide to Compliance: How To Get Compliant and Stay Agile
Red team testing: hacking and lying your way to data.
We at Bulletproof provide a range of different cyber security services, including penetration tests, managed SIEM, and compliance consultancy. Though undoubtedly the most interesting (and cool) service we offer are our red team assessments.
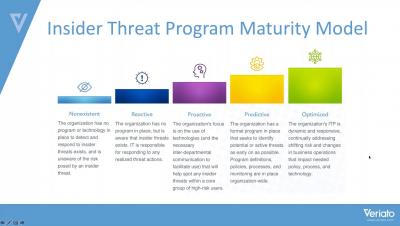
How Mature Is Your Insider Threat Program
How to Create Incident Response Plan Steps for Data Breaches
An estimated 34 percent of companies have experienced data breaches in the last 12 months. With those odds, every organization should be prioritizing cyber security and cyber attack management. Take the time now to put together a data breach incident response plan utilizing these steps, so if your organization is affected, you’ll be able to respond as quickly and effectively as possible. Here are some key steps the plan you create should include.
Abuse MITM possible regardless of HTTPS
Almost ten years ago Firesheep made the news. Security people had known for years the danger of public WiFi-networks, but it was not until someone made a user-friendly Firefox extension out of the idea until it really got people’s attention. Since then a lot has happened to the web, so would something like that still be possible?
Detectify security updates for 29 November
For continuous coverage, we push out major Detectify security updates every two weeks, keeping our tool up-to-date with new findings, features and improvements sourced from our security researchers and Crowdsource ethical hacker community. Due to confidentially agreements, we cannot publicize all security update releases here but they are immediately added to our scanner and available to all users. This post highlights a few things that we have improved in the last two weeks.
Announcing: MOXIS QuickSign for Egnyte Connect
If a paperless future is on your enterprise’s digital roadmap, the new integration between MOXIS and Egnyte will be music to your ears. That’s right, today we are excited to announce a new eSignature integration for Egnyte Connect – MOXIS QuickSign.
November turns bad for Microsoft & Instagram!
Data breach is a major player when it comes to causing financial as well as reputational losses to a business. With the implementation of laws such as GDPR and a plethora of privacy debates going across the globe, unethical data collection or poor coding practices are the new players in the town. In the last two weeks, Microsoft and Instagram have been in the news – one for collecting MS Office user data while other for displaying passwords in the plain text.
S3 Security Is Flawed By Design
Amazon S3, one of the leading cloud storage solutions, is used by companies all over the world to power their IT operations. Over four years, UpGuard has detected thousands of S3-related data breaches caused by the incorrect configuration of S3 security settings. Jeff Barr, Chief Evangelist for Amazon Web Services recently announced public access settings for S3 buckets, a new feature designed to help AWS customers stop the epidemic of data breaches caused by incorrect S3 security settings.