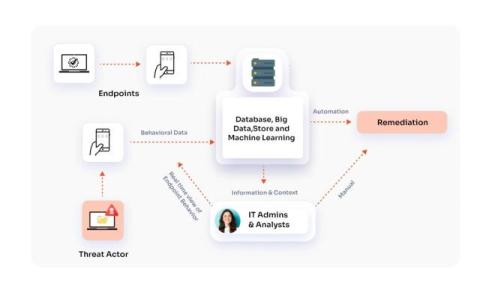
What is EDR in Cyber Security?
Ever wondered how to keep your business safe from the ever-growing wave of cyber threats? Let’s understand what Endpoint Detection and Response (EDR) is and how it can be a trusted ally in protecting your business online.