Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
SCA
CyberArk SCA Slack Workflow Approval (Part 2)
Automated SCM project scanning with Black Duck SCA | Synopsys
CyberArk SCA Slack Workflow Approval (Part 1)
What is SCA (Software Composition Analysis) software?
Announcing a Unified Veracode SAST and SCA IDE Plugin
Accelerate modern development with Polaris pull request comments support | Synopsys
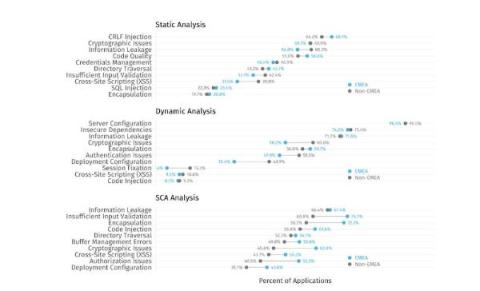
New EMEA Software Security Data Demonstrates Necessity of SCA
New software security data demonstrates that Software Composition Analysis (SCA) will help bolster the safety and integrity of open-source software usage for organizations in the Europe, Middle East, and Africa (EMEA) region in particular. The EU Cyber Resilience Act makes this research especially crucial and timely. Let’s dive in and look at recommendations for EMEA teams wanting to secure cloud-native development.
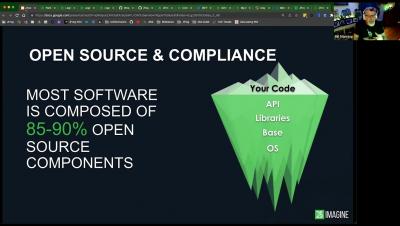
Why SCA is Critical for Securing the Software Supply Chain
Weaknesses within software supply chains create a foothold for exploitation from cyberattacks. The problem is so significant that even the White House released an Executive Order that speaks directly on this topic. “The Federal Government must take action to rapidly improve the security and integrity of the software supply chain,” states the Executive Order emphatically. Now, you may be wondering what your organization can do to mitigate this risk.