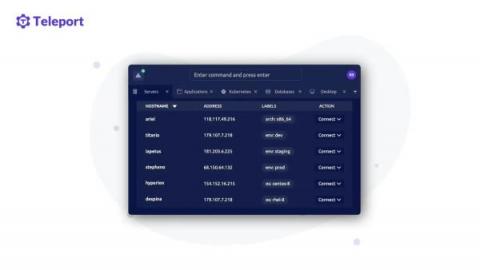
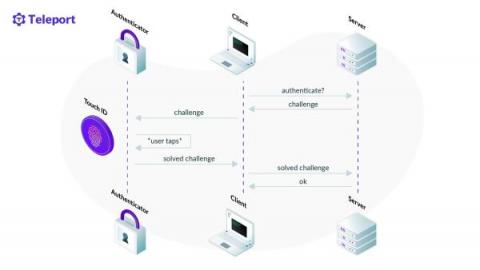
Cockroach Labs and Teleport - Hyper-Scale Your Database Without Sacrificing Security
According to a recent Gartner study, the fast pace of change across technologies, organizational priorities, business opportunities and risks requires identity and access management architectures to be more flexible. As digital business relies on digital trust, security and identity are — more than ever — an essential foundation of an organization’s business ecosystem.