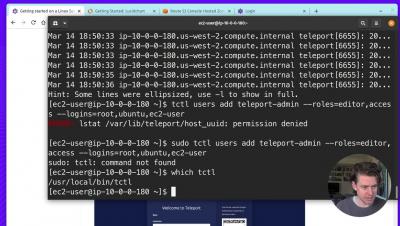
Secure Bots and Service Account Access With Ephemeral Certificates
"Create cryptographically secure access keys" and "Rotate keys frequently" — These are probably the best security recommendations one can get for bot authentication security. In reality, while these are good practices, they simply aren't enough. First, cryptographically secure keys only prevent simple guessable or brute-force attacks, but the impact is catastrophic if the keys themselves are stolen.