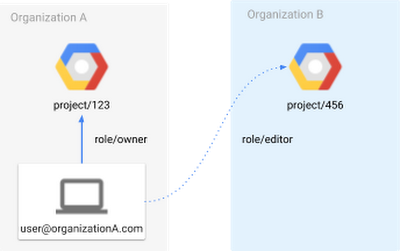
Making it Rain - Cryptocurrency Mining Attacks in the Cloud
Organizations of all sizes have made considerable shifts to using cloud-based infrastructure for their day-to-day business operations. However, cloud security hasn't always kept up with cloud adoption, and that leaves security gaps that hackers are more than happy to take advantage of.