Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Arctic Wolf Observes Threat Campaign Targeting Palo Alto Networks Firewall Devices
On November 18, 2024, Palo Alto Networks disclosed the existence of two vulnerabilities (CVE-2024-0012 and CVE-2024-9474) in Palo Alto Networks OS (PAN-OS), the operating system used on their firewall devices. A day later, watchTowr released a report providing technical details on how to chain the two vulnerabilities together to achieve remote code execution of these vulnerabilities.
Increasing Organic Traffic with User-Friendly Site Builders
Creating an effective online presence is vital for businesses and individuals aiming to thrive in a competitive digital landscape. One of the most significant factors in this endeavour is driving organic traffic to your website. User-friendly site builders play a crucial role in achieving this goal by simplifying the web development process while offering tools that enhance visibility and engagement.
5 Key Differences Between Proxies and Firewalls
The world has never been this hyper-connected, but here's the bad side: if you are not dealing with one security threat, it's another, from malware and hacking to even lapses by your team. To enhance the protection of sensitive data, you might need more than one tool. Two of the most thrown-around words in this space are firewalls and proxies. To non-tech-savvy eyes, they mean the same thing. But the truth is that they are not!
Top 5 PDF Password Protectors to Keep Your Files Safe
As we know, PDF is the most used file format in professional and educational settings. Even sensitive data, like bank statements, are usually shared in a PDF format. Before sending these sensitive files over to the recipient, it is essential to ensure their safety to protect confidential data. By applying a password, you can safeguard your files from data breaches. Therefore, it is a good idea to password-protect your PDF files using a trustworthy protection tool. Read this article till the end, as it features a list of renowned PDF Password Protectors to help you pick a suitable tool.
ContFRaversy in Ransomland: Tor-based site emerges for new French-speaking RaaS operation "ContFR"
Following the emergence of data-leak sites (DLSs) for extortion groups Kairos, Chort, and Termite, Cyjax has observed the emergence of a Tor-based site belonging to a new French-speaking Ransomware-as-a-Service (RaaS) operation called ’ContFR’. ContFR is potentially referencing well-known ransomware group Conti, whilst incorporating a reference to France.
Optimizing Kubernetes DNS with NodeLocal DNSCache and Calico eBPF: A Practitioner's Guide
In the world of Kubernetes, optimizing cluster performance and reliability is paramount, especially when it comes to fundamental operations like DNS lookups. NodeLocal DNSCache is one such solution that helps reduce DNS latency by caching responses locally on each node. While this tool is effective in standard Kubernetes setups, complications arise when integrating it with advanced networking solutions such as eBPF-based dataplanes.
Top Security Threats Worldwide Q2 2024
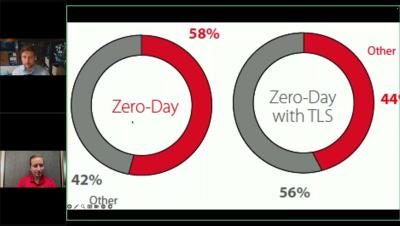
Join WatchGuard CSO Corey Nachreiner and Director of Security Operations Marc Laliberte as they discuss key findings from the WatchGuard Threat Lab’s Q2 2024 Internet Security Report. You’ll learn about the latest malware trends, like malware volume dropping across all products but evasive “zero day” malware increasing. They’ll cover the top network exploits, like a 2019 Nginx vulnerability that threat actors targeted during the quarter. And they will share the most dangerous phishing and malware sites your users visited, and much more.
The Ultimate API Threat Report: How Wallarm Analyzes Attacks #Wallarm #dataanalysis
Discover how Wallarm gathers and analyzes real data on API attacks to create comprehensive security reports. By collecting data from Wallarm’s platform, public repositories, private sources, and security bulletins, Wallarm produces fact-based API threat stats without relying on opinions. This report provides deep insights into API vulnerabilities and attack trends, enhancing Wallarm’s API risk models and improving their security solutions. Download the full report now to stay informed on the latest API threats and protect your APIs effectively.
Planning with AI: Minimizing Uncertainty, Maximizing Trust
Gal Peretz is Head of AI & Data at Torq. Gal accelerates Torq’s AI and data initiatives, applying his deep learning and natural language processing expertise to advance AI-powered security automation. He also co-hosts the LangTalks podcast, which discusses the latest AI and LLM technologies. To stay ahead of today’s threats, you must do more than keep pace — you need to equip your team with tools that enable smarter, faster responses.