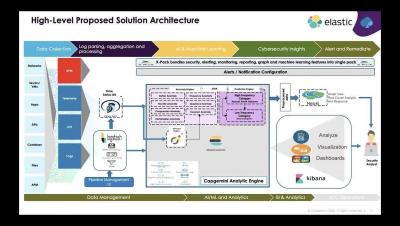
Joint Cybersecurity Advisory on Threat Hunting and Incident Response Released
A joint cybersecurity advisory released on September 1st detailed technical methods for uncovering and responding to malicious activity including best practice mitigations and common missteps. A collaborative effort, this advisory (coded AA20-245A) is the product of research from the cybersecurity organizations of five nations.