Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Logging
Devo Exchange: Accelerating Time to Value for Devo Customers
At Devo, we take pride in providing our customers with innovations that enable them to derive tremendous value from our Platform and applications as they work to keep their organizations secure. That ongoing commitment is embodied in our newest offering — Devo Exchange.
How to Upgrade Graylog V3 to V4 2
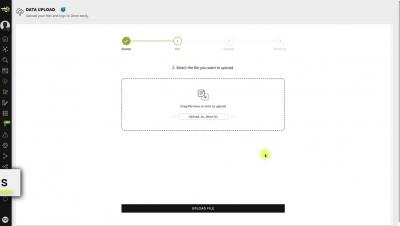
Sending data to Devo - Uploading local data
Optimized Security Traffic Mirroring Examples - Part 1
You have to capture everything to investigate security issues thoroughly, right? More often than not, data that at one time was labeled irrelevant and thrown away is found to be the missing piece of the puzzle when investigating a malicious attacker or the source of an information leak. So, you need to capture every network packet.
Introducing Synthetic Adversarial Log Objects (SALO)
The SURGe team at Splunk is always exploring new methods and tools to make our lives easier. Today we’d like to share some of that work with you. Before we dive into the what and how, I’d like to briefly explain the why.
Devo's Use Case-Driven Approach to Accelerate SIEM Time to Value
Organizations cannot wonder if a data breach will happen — they must prepare for when that day comes. Early detection is key to mitigating an attack when it inevitably occurs, but how can CISOs ensure their teams can sift through all the noise they encounter in the SOC to spot malicious activity? Security information and event management (SIEM) technology can play a critical role in empowering your security team to detect potential indicators of compromise faster.
How To Detect & Mitigate Apache Log4j CVE-2021-44228
If you've already heard about the Apache Log4j CVE-2021-44228 (also known as Log4Shell and formally LogJam) vulnerability then you will know that this is a significant issue as many organisations are scrambling to secure their infrastructure from this critical remote code execution (RCE) vulnerability. With these considerations in mind, we wanted to bring you a guide that outlines the steps that can be followed to ensure the security of your systems from CVE-2021-44228.
Aw, HEC! Splunking Okta's Event Hooks with the HTTP Event Collector
This weekend I spent some time with Okta’s Identity Engine product, learning about various ways to integrate it with Splunk and other external systems. When I got to Okta’s Event Hooks feature, I exclaimed “Aw, HECk!” (actually I said something a little stronger) and banged my head against my old copy of "Log4J 4 Me and U - A Complete Guide" for a few hours trying to get Event Hooks sending data properly into Splunk’s HTTP Event Collector, or HEC.