Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
Kubernetes Version 1.24: Everything You Should Know
Three Benefits Authorization Brings to your Identity Strategy
Organizations today are embracing cloud-native technologies to increase time-to-market, scalability and cost savings. A big part of the cloud-native transition is moving legacy systems and architectures to the cloud. With this comes both complexity and new risks because modern applications are often composed of dozens of microservices, housed in containers and hosted on immutable, dynamically scaling platforms like Kubernetes.
Eliminate noise and prioritize the vulnerabilities that really matter with Risk Spotlight
Is your team drowning in container vulnerability noise? Are you spending a lot of time figuring out where to focus resources on and still missing dangerous vulnerabilities? Know that you are not alone. Container environments revolutionized app development by enabling unprecedented velocity, but not without a price. The use of readily available container images of third-party and open-source code enabled much faster cycles, but also facilitated the introduction of vulnerabilities in the application.
Are vulnerability scores misleading you? Understanding CVSS severity and using them effectively
Vulnerabilities are everywhere. Vetting, mitigating, and remediating them at scale is exhausting for security practitioners. Let’s keep in mind that no organization has the capacity to find and fix all vulnerabilities. The key is to understand what a vulnerability is, interpret the meanings of the CVSS score, and prioritize and effectively use resources within constrained time limits or delivery windows. Since 2016, new vulnerabilities reported each year have nearly tripled.
Customer Spotlight - Civo
For this customer spotlight we're highlighting Civo, a cloud-native service provider focused on Kubernetes. Bulletproof helps keep Civo's platform secure, giving peace of mind to their customers. In this edition we'll learn about Kubernetes and how it's rapidly becoming the de facto standard for managing cloud infrastructure to support modern applications. The COVID-19 pandemic has changed how we do business forever.
Sysdig achieves AWS DevSecOps specialization within AWS DevOps Competency
Sysdig is pleased to announce that it has achieved Amazon Web Services (AWS) DevOps Competency for development, security, and operations (DevSecOps). This designation highlights the value provided by the Sysdig platform to AWS customers to achieve their DevSecOps goals. As a key partner for the ecosystem, Sysdig collaborates closely with AWS and its customers to enhance the protection of cloud infrastructure and applications against continuously evolving security threats.
6 Steps to Complete a Kubernetes Backup Using CloudCasa
We are excited to have Saiyam Pathak, Director of Technical Evangelism at Civo, sign up for CloudCasa and blog the simple steps required to complete a backup and restore of a Kubernetes cluster. For those that don’t know Saiyam, he has a passion for writing and talking about Kubernetes and cloud native technologies to make them more accessible for developers. Saiyam is a CNCF ambassador and a cloud native blogger with his own Cloud Native Simplified YouTube channel.
Learn Microservice Authorization on Styra Academy
Styra Academy, our online training portal for free courses on OPA, Rego, and Styra Declarative Authorization Service, has a new course available - Microservice Authorization! Before diving in, let’s get a better understanding of microservices and some of the authorization challenges developers need to consider. Microservices are everywhere — and securing them presents a unique set of challenges.
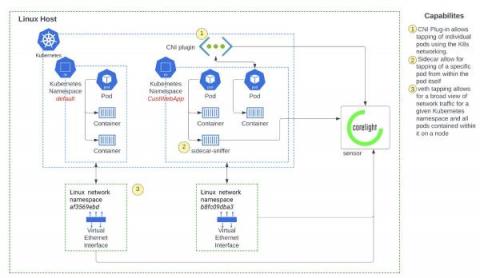
Deeper visibility into Kubernetes environments with network monitoring
Network monitoring solutions can overcome the security visibility blind spots in Kubernetes environments, by providing a source of truth for SOC analysts. Container security solutions broadly span the spectrum of (a) prevention - securing the container image and ensuring the right policies are in place during runtime and (b) detection - monitoring runtime events for threat detection and investigation.