What's New in Sysdig - May 2024
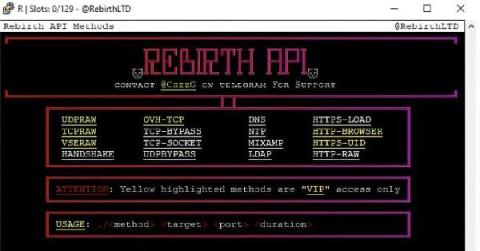
“What’s New in Sysdig” is back with the May 2024 edition! My name is Dustin Krysak. I’m a Customer Solutions Engineer based in Vancouver, BC, and I’m excited to share our latest updates. The Sysdig Threat Research Team (TRT) has been busy recently investigating and analyzing new security threats. Their research has uncovered notable vulnerabilities and attack vectors, which they’ve shared insights about through the Sysdig blog.