Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Defend against insider threats with LimaCharlie
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) defines insider threat as “the potential for an insider to use their authorized access or understanding of an organization to harm that organization.” The nature of insider threats is fairly wide-ranging. Most of us in the security field will naturally think of insider threats in cybersecurity terms, but CISA’s definition includes things like espionage, terrorism, and workplace violence.
Weekly Cyber Security News 30/03/2023
A selection of this week’s more interesting vulnerability disclosures and cyber security news. For a daily selection see our twitter feed at #ionCube24. If during the past week you panicked when you went to do a push to git, and saw the alarm that your connection could be compromised, don’t worry, github just rotated keys because…
How to reduce your RPO and recover rapidly from failure on your K8s Cluster with Trilio and Mirantis
Employee Rewards Automation: A Case Study of Exposed PII in Power Automate
In recent years, companies have been looking for ways to streamline their HR processes and make them more efficient. In recent years it has become practically feasible for business users such as HR professionals to create their own solutions, due to the wave of citizen development which is exploding worldwide. Huge market players perceive this as a growth area and are heavily investing in providing solutions and platforms to enable business users to build what they need, when they need it.
More Security. Less Tool Switching
“Well, yeah, I can give the devs a new security tool, but I can’t make them use it.” I was mid-way through dinner with an old college friend when he dropped this into the conversation. I’d told him I wanted to pick his brain about security issues and tools, but told him no matter what, I wouldn’t start to deliver a pitch. Well, I kept my promise, but I think I must have given my tongue a bruise from biting it.
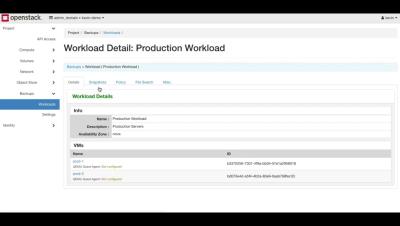
OpenStack Tutorial: How to One-Click Restore OpenStack Workloads with Trilio
Enhanced security in JFrog Artifactory using Bytesafe
In the ever-evolving world of software development, secure and efficient package management is crucial to maintaining code integrity and fostering collaboration. While JFrog Artifactory offers a powerful solution for repository management, integrating Bytesafe as an upstream source can further enhance security and collaboration capabilities.
Anonymous Sudan: Religious Hacktivists or Russian Front Group?
The Trustwave SpiderLabs research team has been tracking a new threat group calling itself Anonymous Sudan, which has carried out a series of Distributed Denial of Service (DDoS) attacks against Swedish, Dutch, Australian, and German organizations purportedly in retaliation for anti-Muslim activity that had taken place in those countries.
Effective Cloud Incident Response: Fundamentals and Key Considerations
Human error behind misconfigurations, a host of insecure remote access issues, exposed business credentials with reused passwords and unpatched vulnerabilities have all contributed to a significant increase in cloud security incidents. Many organizations don’t foresee the challenges of what it will take to protect their data and operations after a move to the cloud.