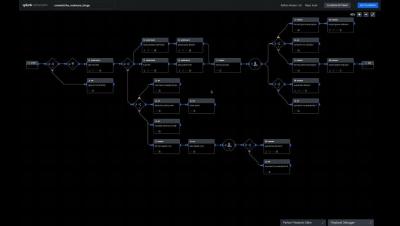
Splunk for OT Security V2: SOAR and More
In the last 90 days, the news of cyberattacks on critical infrastructure has been stunning. From the unprecedented breach represented by Sunburst to the more recent bone-chilling attack at the Oldsmar water facility, the urgency to secure critical infrastructure in transportation, utilities, energy, water, critical manufacturing, telecommunications, healthcare, government facilities and the defense sector has never been higher.