Denmark's Largest Utility Company Accelerates Incident Response
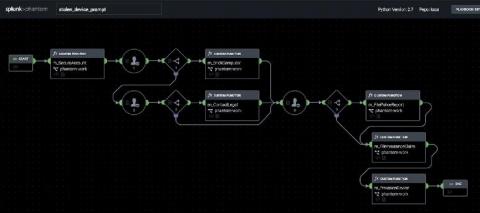
As Denmark’s largest power, utility and telecommunications company servicing 1.5 million customers, Norlys understands the need for fast response to security alerts. When the company first started, the Norlys security team built their own log analytics and incident response capabilities from the ground up. This homegrown approach presented challenges, including manual workflows, too many repetitive tasks and difficult-to-maintain processes.