Unified Controls | Tigera
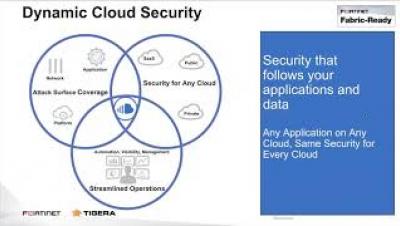
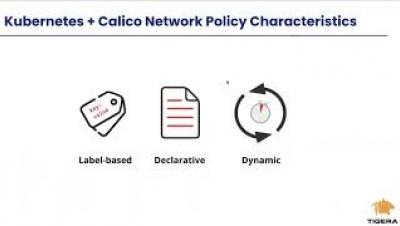
Organizations are scaling Kubernetes deployments with container platforms running on a mix of on-prem, cloud, and multi-cloud infrastructure. However, not all users are taking a standardized approach to building multiple clusters on a common distribution and on a single infrastructure with common security tools.