Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest Videos
Why I decided to start a career in sales - Sophie
Find out more about our products at: https://www.egress.com/products
Why I decided to start a career in sales - Marko
Find out more about our products at: https://www.egress.com/products
Upgrade your Cyber Security Strategy with These 10 Steps
Your cyber security strategy should help you move from a reactive to a proactive approach to cybersecurity. This strategy should include a security foundation that will help you form your plan of action that will result in the prevention of the theft of organizational and employee data. Your cyber security strategy should be as important as your legal, regulatory, financial, or operational strategy. Here are 10 steps to help define and communicate your strategy.
Enhancing Observability in DevSecOps
Digital transformation often accelerates innovation at the expense of creating an intelligence gap with massive amounts of unanalyzed data. This is where Continuous Intelligence comes into play. Join Sumo Logic’s Systems Engineer, Suresh Govindachetty, as he demonstrates how Continuous Intelligence helps find and solve information gaps, and how a single platform approach allows organisations to combine devs, operations, and security in ways that ease the burden for all teams across the organisation.
Veracode Origin Story
Hear from our Co-Founder and Chief Technology Officer, Chris Wysopal, and our Chief Executive Officer, Sam King, on how Veracode was started and why it's a SaaS-based company. The video also outlines our mission of helping customers secure their software.
How To Start A Scan On Kondukto?
Watch this guide to start a scan on Kondukto in 2 min.
Sumo Logic Cloud SIEM overview
Sumo Logic's Cloud SIEM solution provides security analysts with enhanced visibility to seamlessly monitor their on-prem, hybrid, and multi-cloud infrastructures and thoroughly understand the impact and context of an attack. In addition to supporting a wide spectrum of security use cases, including audit & compliance, Sumo Logic fused analytics and SOC automation to perform security analyst workflows and automatically triage alerts—increasing human efficiencies and enabling analysts to focus on higher-value security functions.
Human Layer Security Live - Quantifying human risk: The first step to a secure future - Ed Amoroso
Ed Amoroso, CEO at TAG Cyber LLC and former-CISO at AT&T Research shows sensitive data is put at risk due to email usage every 1.5 days – but in reality, this figure is much higher. That’s because more than half of CISOs rely on employees and their recipients to report email data breaches, despite this approach being inherently unreliable. As a result, CISOs are unable to accurately measure insider risk and deploy technology to properly mitigate it.
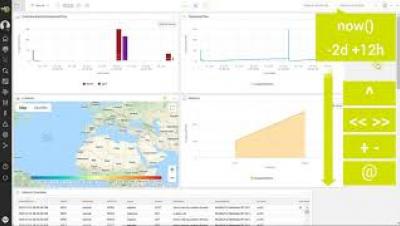
Activeboards Calendars - Setting time ranges manually
Table of Contents:
00:00 - Introduction
01:02 - Setting absolute time ranges
01:49 - Setting relative and snap to time ranges
02:21 - Time expressions example 1
02:56 - Time expressions example 2
03:26 - Omitted periods in time ranges