Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
GDPR and Biometric Data: Ethical Considerations and Privacy Implications
As technology advances and the use of biometric data becomes more prevalent, it is crucial to address the privacy concerns and regulatory compliance associated with this sensitive data. The General Data Protection Regulation (GDPR) plays a key role in safeguarding individuals’ privacy rights and ensuring the responsible handling of biometric data. Artificial Intelligence (AI) can also be utilized to ensure compliance and responsible handling of biometric data.
Securing Critical Infrastructures in Germany: Navigating KRITIS Regulation
Germany is widely acknowledged as one of the most technologically advanced nations. However, this prominence also implies a significant reliance on its critical infrastructures (KRITIS), which are essential to the smooth operation of the state and society. To safeguard these infrastructures, Germany has enacted new laws, IT Security Act 2.0 and KRITIS Regulation 2.0, that aim to improve the security of IT systems.
Visualizing Trust Assurance: The Story Behind Our New Look
Customers come to us for many reasons: to spend less time preparing for audits and answering security questionnaires, to prove their impact to their boss and board, to log into fewer systems, to save money, to strengthen their security posture, to make it easier for their colleagues to support compliance efforts – to name a few.
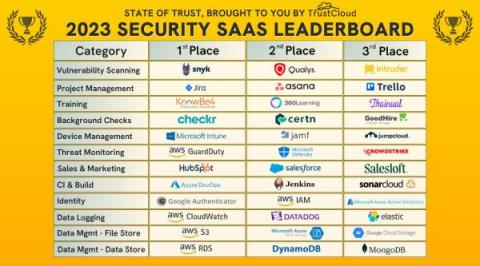
State of Trust Insights: The 2023 Security SaaS Leaderboard
TrustCloud is proud to present the 2023 Security SaaS Leaderboard – a list of the most popular vendors for security- and trust-related programs, based on analysis of the software platforms our customers are connecting to on the path to trust assurance.
What the EU NIS2 Directive Is and How to Be NIS2 Compliant
In the dynamic and ever-shifting realm of cybersecurity, the Directive on measures for a high common level of cybersecurity across the Union (NIS2 Directive) has emerged as a cornerstone framework, designed to ensure the safety of critical network and information systems across the European Union. This recent directive, which has entered into force, holds considerable significance, casting far-reaching implications for diverse sectors and entities operating within the EU.
Understanding the Fair Credit Reporting Act (FCRA)
The Benefits of Managed Security Services
If your company is not using managed network security services, then it's time to start. Here are the benefits of managed security for your business.
Centralized Log Management for TISAX Compliance
How Vanta uses Okta for identity and access management
In this series, you’ll hear directly from Vanta’s own Security, Enterprise Engineering, and Privacy, Risk, & Compliance Teams to learn about the team’s approach to keeping Vanta secure. We’ll also share some guidance for teams of all sizes — whether you’re just getting started or looking to uplevel your operations.