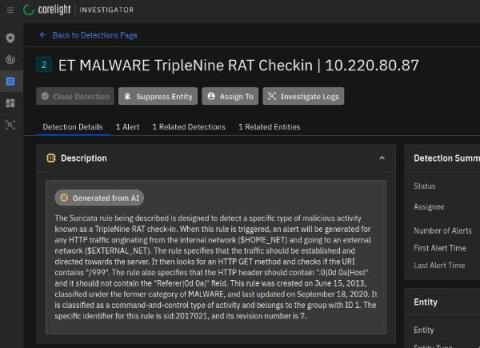
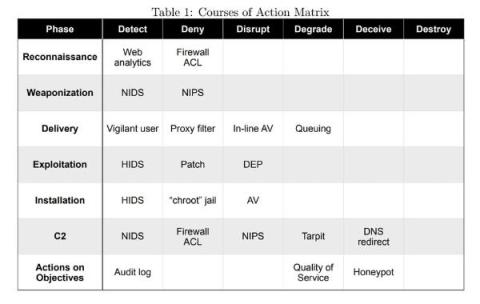
The Art of Team Building: Blueprints from the Black Hat NOC
It has been a distinct honor to be a part of the Corelight team that helped defend this year’s Black Hat events. I started the event season in the Network Operations Center (NOC) at Black Hat Asia, and then capped it off at Black Hat in Las Vegas. In this blog I’ll share my experience and learnings from participating in both NOCs.