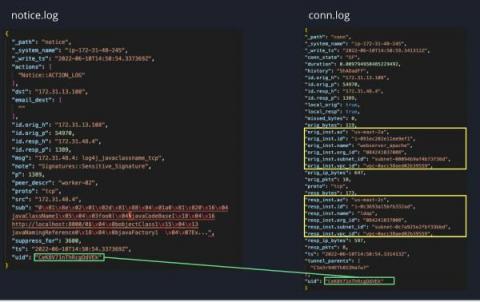
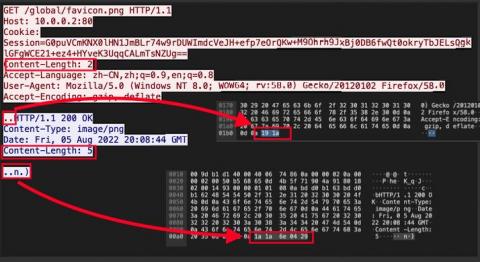
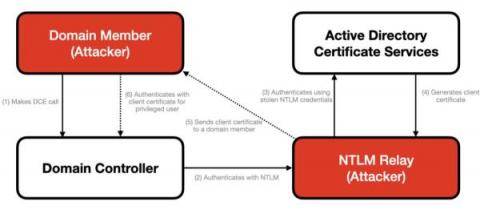
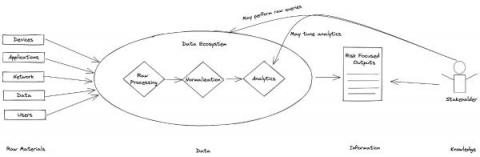
Zeek on Windows
As we shared at ZeekWeek 2022 in October, we’re thrilled to announce emerging support for Zeek on Windows, thanks to an open-source contribution from Microsoft. Part of its integration of Zeek into its Defender for Endpoint security platform, this contribution provides fully-native build support for Windows platforms and opens up a range of future technical possibilities in this vast ecosystem.