How to Secure Amazon RDS Access With an Identity-Aware Access Proxy
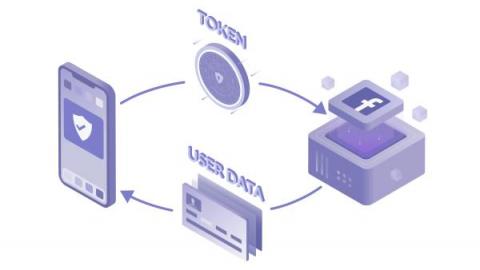
Databases are sensitive resources that need an additional layer of protection and security. Though database servers have built-in authentication and authorization mechanisms, they are not designed for cloud-based, multi-tenant access mechanisms. Managed databases such as Amazon RDS are accessed and administered by different personas with varying levels of access permissions.