Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Cloud
Survey: 84% of Security Pros Said Their Organizations Struggled to Maintain Security Configurations in the Cloud
Headlines continue to suggest that organizations’ cloud environments make for tantalizing targets for digital attackers. Illustrating this point, the 2019 SANS State of Cloud Security survey found “a significant increase in unauthorized access by outsiders into cloud environments or to cloud assets” between 2017 (12 percent) and 2018 (19 percent). These findings beg the question: how prepared are organizations to defend themselves against cloud-based threats?
Forensics in the Cloud: What You Need to Know
Cloud computing has transformed the IT industry, as services can now be deployed in a fraction of the time that it used to take. Scalable computing solutions have spawned large cloud computing companies such as Amazon Web Services (AWS), Google Cloud and Microsoft Azure.
Multi-Cloud Security Myths
Best Practices for IT Security Teams in the Age of Cloud
About a decade ago, organizations were hesitant to adopt cloud solutions, with many citing security concerns. Fast forward to 2019, and 81% of organizations have a multi-cloud strategy, spurred on by the desire for increased flexibility, usage-based spending and desire to respond to market opportunity with greater agility.
Moving to the Cloud and How You Shift Your Security Management Strategy
As someone who has worked for their entire career in the Managed Network Services space, if I had to pick out, over the past five years, two of the most impactful shifts in managing technology, it would be a shift from traditional, in-house servers to solutions where 3rd parties build “clouds” to provide similar business functions as well as the increased pressure on organizations to have comprehensive cyber-security strategies as threats become more significant.
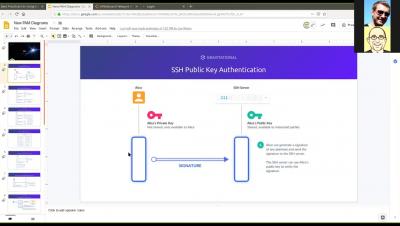
Using AWS Session Manager with Enhanced SSH and SCP Capability
Amazon Web Services recently announced new capabilities in the AWS Systems Manager Session Manager. Users are now capable of tunneling SSH (Secure Shell) and SCP (Secure Copy) connections directly from a local client without the need for the AWS management console. For years, users have relied on firewalls and bastion hosts in order to securely access cloud assets, but these options have security and management overhead tradeoffs.
Multi-Cloud Security Best Practices Guide
A multi-cloud network is a cloud network that consists of more than one cloud services provider. A straightforward type of multi-cloud network involves multiple infrastructure as a service (IaaS) vendors. For example, you could have some of your cloud network’s servers and physical network provided by Amazon Web Services (AWS), but you’ve integrated that with your servers and physical networking that’s provided by Microsoft Azure.
Best Practices for Teleport with SSH & Kubernetes
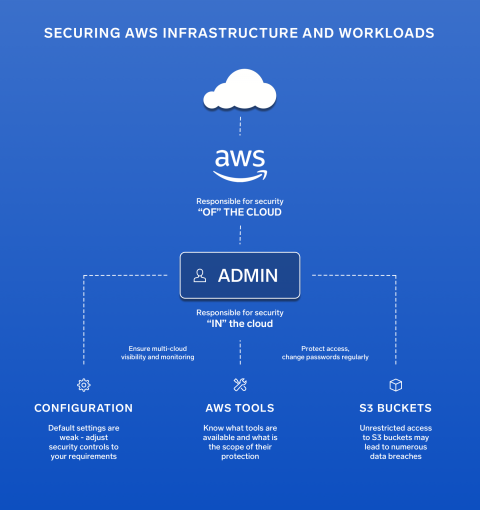
Why you need to secure your AWS infrastructure and workloads?
Enterprises are increasingly adopting a cloud-first approach and migrating their workloads, data and applications to the Cloud. Amazon Web Services continues to lead the Public Cloud industry with more than 30% of the market. As digital transformation progresses and the digital space expands, so does the attack surface that exposes the ongoing proliferation of security risks. In today’s cloud-first world, security remains the primary concern.