Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
September 2020
Joint "CYPRES" Report on Incident Response Released by FERC
Earlier this month, the Federal Energy Regulatory Commission (FERC) published a joint report entitled “Cyber Planning Response and Recovery Study” (CYPRES) in partnership with the North American Electric Reliability Corporation (NERC) and eight of its Regional Entities (REs) in order to review the methods for responding to a cybersecurity event.
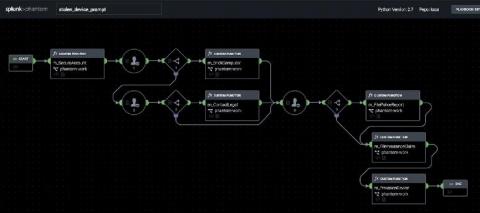
Adaptable Incident Response With Splunk Phantom Modular Workbooks
Splunk Phantom is a security orchestration, automation and response (SOAR) technology that lets customers automate repetitive security tasks, accelerate alert triage, and improve SOC efficiency. Case management features are also built into Phantom, including “workbooks,” that allow you to codify your security standard operating procedures into reusable templates.
What is Incident Response?
As new types of security incidents are discovered, it is absolutely critical for an organization to respond quickly and effectively when an attack occurs. When both personal and business data are at risk of being compromised, the ability to detect and respond to advanced threats before they impact your business is of the utmost importance.