Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
April 2023
Fake Meta Tech Support Profiles for Fraud
Researchers at Group-IB have found an extensive campaign in which criminal operators have created a large number of fake Facebook profiles that repost messages in which the scammers misrepresent themselves as tech support personnel from Meta (Facebook’s corporate parent). Researchers discovered some 3200 bogus profiles in twenty-three languages. By far most of the profiles were created in English, more than 90%, followed by Mongolian (2.5%), Arabic (2.3%), Italian (0.8%), and Khmer (0.6%).
Wells Fargo Scam Texts: How To Spot Them
Texting has taken over the global communication space; marketers and predators are seeing huge dollar signs. Email continues to be a reliable, but somewhat fraught with problems, alternative form of communication. In fact, the average user interacts, sends, and receives 25% more texts than email, and usage is skyrocketing. Most electronic device users have loads more unopened emails than texts.
FBI Warns of Sextortion Scams that Yield a New Equally Scam-Like Service: Sextortion Assistance
A FBI bulletin highlights a new twist in the sextortion game: companies claiming to assist with addressing sextortion who use deceptive social engineering tactics to coerce victims into paying huge fees.
Fraudulent Tax Filings Go Out For Harding, Shymanski, and Company Customers
Harding, Shymanski, and Company is a major accounting firm that works with customers providing them with tax help and other financial services. The company recently suffered from a data breach that exposed many of its clients and led to fraudulent tax filings for the 2022 tax year. The company employs more than 142 people and has an approximate annual revenue of $28 million. A large number of individuals were impacted by this very serious data breach.
Massive Investment Fraud Ring Stole Over Euro89M From Thousands of Victims
Read also: Bitrue crypto platform hacked for $23 million, Ryuk crypto broker sentenced to no jail time, and more.
FTC accuses payments firm of knowingly assisting tech support scammers
Multinational payment processing firm Nexway has been rapped across the knuckles by the US authorities, who claim that the firm knowingly processed fraudulent credit card payments on behalf of tech support scammers. A Federal Trade Commission (FTC) complaint argues that Nexway and its subsidiaries broke the law by helping scammers cheat money from unsuspecting consumers.
That Email Isn't from the New Jersey Attorney General
Earlier this month, state employees in the US state of New Jersey began receiving emails that falsely represented themselves as originating with the state’s attorney general. “At first blush, the communiques appeared to come from the state Attorney General's Office and sported a convincing njoag.gov domain.
What is SIM Swapping?
SIM swapping is when a cybercriminal impersonates someone in order to convince a mobile carrier to activate a new SIM card. These bad actors use social engineering tactics, claiming “their phone” was supposedly lost, stolen or damaged, when in reality, it was never their phone to begin with. When a cybercriminal successfully SIM swaps, they can more easily steal someone’s identity because they can now receive their text messages and phone calls.
Safeguarding the Most Vulnerable in Society from EBT Fraud
Back in 1939, Henry Wallace, the American Secretary of Agriculture, created the Food Stamp Program. It was designed to supply surplus agricultural commodities to American families in need during the Great Depression. People who received public assistance could get stamps that were then used to purchase food. The program underwent several iterations in the 1960s, ’70s, and ’80s until finally, in 1984, the first Electronic Benefits Transfer (EBT) system was introduced.
London NatWest Bank Warns Customers of Alarming Impersonation Scams
National Westminster Bank, the London-based bank familiarly known as NatWest, has warned its customers to be on the alert for emails pretending to be from NatWest, but which in fact are from scammers trying to bubble the unwary out of their savings.
Beware of Agreement Fraud: Scammers Targeting CEO's with Agreement Draft
Introduction: Fraudulent campaigns aimed at top-level executives through phishing are on the rise. In this technical blog post, we will delve into a particular type of CEO phishing scam that employs an attachment containing an agreement draft. We will examine the attack's technical aspects and suggest preventive measures that businesses can adopt to safeguard themselves.
Glamourizing fraudsters hurts victims of fraud, and society
We seem to be fascinated by fraudsters, and recent documentaries prove this. The documentary landscape is populated with many fraud-centered stories, such as The Tinder Swindler, Fyre, The Con, Fake Heiress, The Inventor, and many others. Some have even been made into series, such as the story of Elisabeth Holmes in The Dropout, and the story of Anna Delvey in Inventing Anna. We just can’t get enough of it, and who can blame us? These stories are fascinating, entertaining, and engaging.
Common OfferUp Scams to Watch Out For
One of the hottest online trends is auction sites selling everything from toys to cars and items tucked away in a closet. Sites such as Facebook Marketplace, Craigslist, and Decluttr, provide a way for anyone to sell anything. eBay and Craigslist began the craze of selling unwanted household items back in 1995. These sites sought to bring together buyers and sellers in an open and honest marketplace. Both companies expanded rapidly beyond collectibles into any saleable item.
Large Language Models Will Change How ChatGPT and Other AI Tools Revolutionize Email Scams
The use of Large Language Models (LLMs) is the fine tuning AI engines like ChatGPT need to focus the scam email output to only effective content that results in a wave of new email scams.
Common Etsy Scams to Avoid
Etsy, since 2005, has been a marketplace for millions of small business owners, selling everything from jewelry to toys. Without a doubt, an online criminal is lurking around every virtual corner. It is estimated that nearly six to eight million individual shop owners are doing business on the Etsy platform. One of the significant aspects of using Etsy to sell your goods is they offer fraud protection in which they pay for any fraudulent transaction under $250.
What does Genesis Market's demise mean for other sites selling digital identities?
As reported widely in the press, the Genesis Market is no more. On Tuesday 4th April 2023, the FBI seized control of the infamous marketplace that’d had hundreds of thousands of stolen digital identities for sale, replacing its login page with a takedown notice and call for further information from its users.
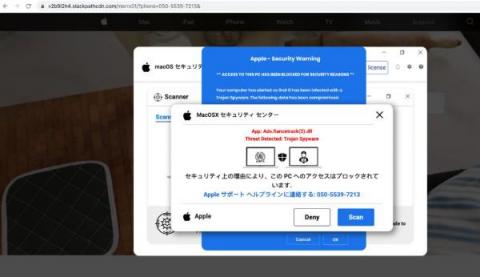
Tech Support Scam Pivots from DigitalOcean to StackPath CDN
Attackers who were previously abusing DigitalOcean to host a tech support scam have expanded the operation, now abusing StackPath CDN to distribute the scam, and are likely to start abusing additional cloud services to deliver the scam in the near future. From February 1 to March 16, Netskope Threat Labs has seen a 10x increase of traffic to tech support scam pages delivered by StackPath CDN.
That's Not Actually Mr. Musk, That's a Scam
A school principal in Volusia County, Florida has resigned after sending $100,000 to a scammer posing as Elon Musk, WESH 2 News reports. Dr. Jan McGee from the Burns Science and Technology Charter School had been in communication with the individual for four months, even though her colleagues warned her that it was a scam. “McGee told a packed audience she was taken in by a fake Elon Musk, someone posing online as the space pioneer,” WESH 2 says.
Chinese fraudsters: evading detection and monetizing stolen credit card information
Cyber attacks are common occurrences that often make headlines, but the leakage of personal information, particularly credit card data, can have severe consequences for individuals. It is essential to understand the techniques employed by cyber criminals to steal this sensitive information.
Fake ChatGPT Scam Turns into a Fraudulent Money-Making Scheme
Using the lure of ChatGPT’s AI as a means to find new ways to make money, scammers trick victims using a phishing-turned-vishing attack that eventually takes victim’s money. It’s probably safe to guess that anyone reading this article has either played with ChatGPT directly or has seen examples of its use on social media. The idea of being able to ask simple questions and get world-class expert answers in just about any area of knowledge is staggering.
5 Secure Ways to Avoid Crypto Theft in 2023
The rise in popularity of cryptocurrencies has brought about significant concerns regarding wallet vulnerabilities and digital theft among individuals and businesses transacting in the market. While the meteoric rise in the value of cryptocurrency has attracted legitimate investors, it has also caught the attention of malicious actors who are constantly searching for vulnerabilities to exploit.