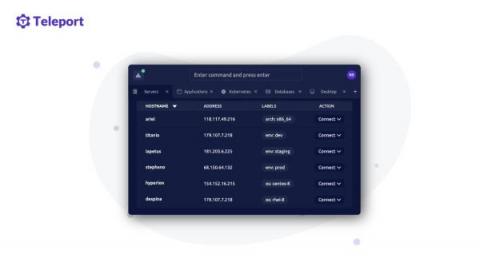
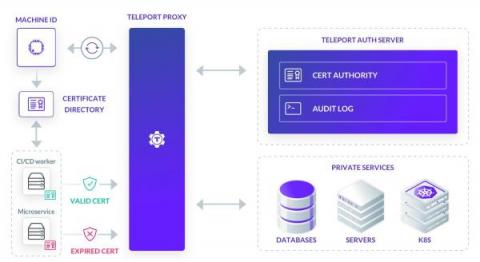
On terminals and sessions
In this post I will be announcing a new open source project: Teleport Connect. It is a dedicated secure web browser for accessing cloud infrastructure. But first, let me explain why we've decided to build it, starting with a bit of historical context. As a kid I have always enjoyed imagining the process of programming to having a conversation with a machine. The REPL loop is the most obvious example of this interaction. As our code grows it no longer fits in a REPL environment.