Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
Cloud Security: Messy Blobs and Leaky Buckets
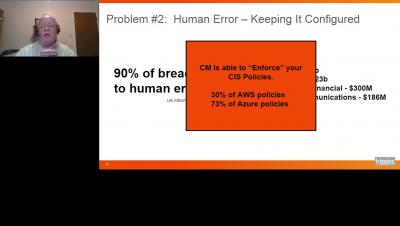
Moving to the cloud means a lot more than just moving your servers and applications to the cloud; it’s also about the data – and data always has a target on it. A lot of IT departments are finding that it’s easier to meet the “five nines” (99.999%) of uptime and availability by going outside their organization and letting AWS, Microsoft, or Google handle the infrastructure and personnel needed to meet those requirements.
A New Vision for Secure Web Gateways
In the recently released 2020 Gartner Magic Quadrant for Secure Web Gateways (SWG) report, Netskope was recognized as a visionary, entering a decades-old legacy security solution area first defined by proxy cache appliances. Times have changed since human rating labs, regional web filtering lists, the use of ICAP for threat and data protection of files, web object caching, bandwidth management, and scripting policies to filter out undesired web objects.
3 Mobile App Security Recommendations for National App Day
On December 11, 2017, Platinum Edge Media and its founder CJ Thompson created National App Day as a way to celebrate how apps have inspired us and changed our culture. The Registrar at National Day Calendar went on to proclaim National App Day to be observed annually. We can’t truly appreciate the impact that apps have on our lives without an idea of how to use these programs securely.
12 Hybrid Cloud Security Threats That You Can Fix
Unify Access to Cloud - Iterating on Identity-Based Management
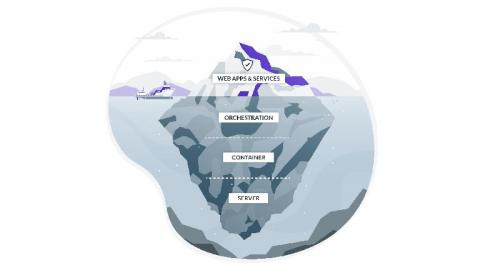
The maturation of software development has been driven by the increasing segmentation of functions into their own portable environments. Infrastructure is splintered into dozens of computing resources, physical servers, containers, databases, Kubernetes pods, dashboards, etc. Such compartmentalization has made it incredibly simple for developers to enter their desired environments with minimal disruption to other working parts.
The Olympics and Burner Phones: Are You Sure About the Safety of That QR Code?
As businesses try to create a contactless experience amid the coronavirus pandemic, many have turned to QR codes. We’re seeing a lot of restaurants using them to display their menus on smartphones and on receipts for a contactless pay option. Within popular apps like Snapchat and WhatsApp, QR codes are an integral part of the user experience. Users can use codes to sign into their account, exchange contact information and make money transfer.
Six key findings from the 'DevSecOps Practices and Open Source Management in 2020' report
This week Synopsys released the “DevSecOps Practices and Open Source Management in 2020” report, findings from a survey of 1,500 IT professionals working in cyber security, software development, software engineering, and web development. The report explores the strategies that organizations around the world are using to address open source vulnerability management, as well as the problem of outdated or abandoned open source components in commercial code.