Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Corelight
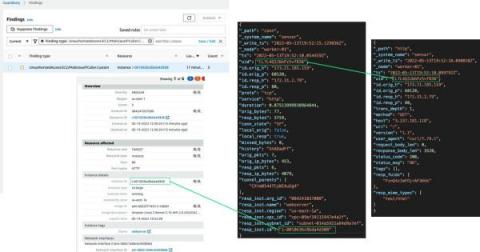
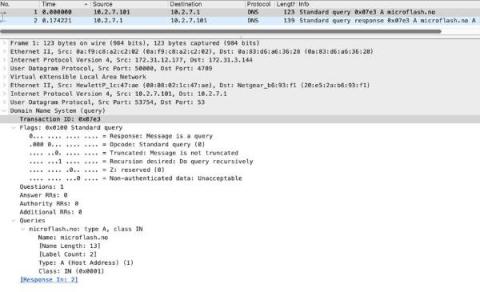
Detections and Findings using Corelight in the Black Hat Asia NOC
As promised, we wanted to dedicate a blog to detections and findings from the network operations center (NOC) at Black Hat Asia 2023 as a follow up to our Lessons Learned blog. Some of these discoveries may not surprise the seasoned analyst or senior threat hunter – but will hopefully provide a little entertainment, because the more things change, the more they stay the same.
Detecting Storm-0558 using Corelight evidence
While there have been many intrusions, compromises, breaches, and incidents that have made news in the IT and InfoSec industries throughout 2022 and into this year, when events or threats like Storm-0558 gain coverage by mainstream media, we often get questions about Corelight’s ability to detect threats through our sensors, products & platform.
I have trust issues and so does my CISO
Trust is hard to earn but necessary for any successful relationship. As organizations build the systems to support Zero Trust, they find themselves balancing security and functionality across their operations. Incident Response and Network Operations in particular can be full of traumatic experiences, and as we sink into those moments the typical responses are freeze, flight, or fight.
Corelight CEO, Brian Dye talks to NYSE's Trinity Chavez on 'The Cyber Series'
How SOCs can level up their PCAP game with Smart PCAP (Part 2)
In terms of unencrypted traffic, several highly used protocols lend themselves to logging and can significantly reduce the burden of packet capture without lowering the fidelity of information or the capabilities of analysts.
Extending visibility through our new ICS/OT collection
Increasingly, security teams are tasked with identifying, understanding, and managing risk around devices that may live outside the traditional IT umbrella. Operational Technology (OT) refers to computing systems that are used to manage and process operational functions as opposed to administrative operations, with Industrial Control Systems (ICS) being a major segment of that OT sector.
Lessons Learned Deploying Corelight in the Black Hat Asia NOC
Last month, Corelight had the distinct privilege of joining Cisco, NetWitness, Palo Alto Networks, Arista, and our internet service provider, MyRepublic, to provide availability and network security overwatch to the Black Hat Asia network in Singapore. This marked our first appearance in the Black Hat Network Operations Center (NOC).
I have Trust Issues and So Does My CISO How NDR can help identify issues in your ZTA
Celebrating CrowdStrike's New Network Detection Service "Powered by Corelight"
Several months ago, we announced that our strategic alliance partner CrowdStrike decided to use our Open NDR technology across its professional services portfolio. This wasn’t just a meaningful validation for us—it was also a testament to the importance CrowdStrike places in arming its world-class Services teams with the technology that can best ensure the protection of its customers.