Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Penetration Testing
An overview of our vulnerability assessment and pentesting process | Cyphere
20 Best Penetration Testing Tools
In recent times when data breaches and cyber attacks have become so common, being cyber resilient and prepared for the attack when it happens is the new norm.
What is Penetration Testing?
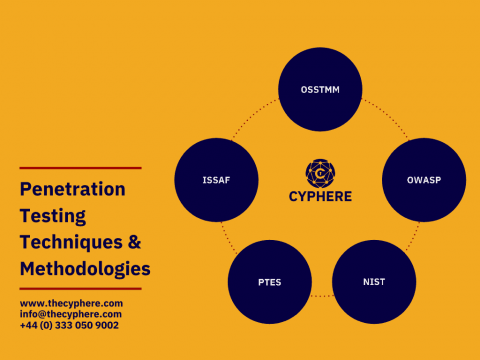
A Penetration Test commonly consists of assessing; the confidentiality, integrity and availability of an information system, widely known as the CIA triad. There are numerous penetration testing approaches. This can include black-box testing, white-box testing and grey-box testing which all, in turn, provide remediation advice. However, the three types of testing define different approaches the consultant takes during an assessment and all have different benefits and disadvantages.
Crossword Cybersecurity Plc acquires threat intelligence company, Threat Status Limited
Bypassing MFA: A Pentest Case Study
When a company implements multifactor authentication, the organization is usually confident that it’s using the best system possible. However, not all MFA is built the same and there are times when the MFA solution being implemented is not delivering the protection required.
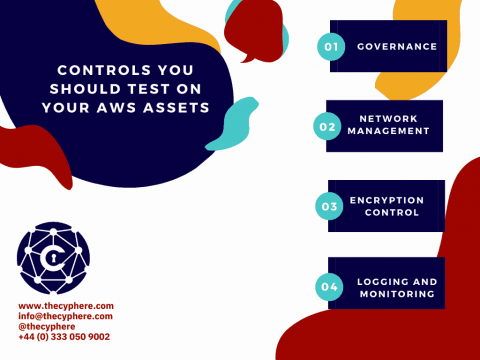
AWS Penetration Testing | All You Need to Know
Amazon Web Services or AWS services has over a million users in around 190 countries and is an ever-growing and widely adopted platform as more and more companies tend to move toward a cloud environment.
Introduction to penetration testing for developers
Developers take a lot of pride in their work. We strive to consistently deliver the best code and avoid dangerous edge-cases. Which is why we aim to detect and remediate bugs before they ship through testing and code reviews. However, when it comes to security, sometimes we fall flat. When a team lacks the proper security tooling, it can stunt development, create extra work, and deliver dangerous security defects to clients and end-users.
How to secure web apps continuously with Pen Testing as a Service
Web applications are continuously evolving due to the hypo-velocity of code changes and stream of new features and functionality leaving businesses exposed to application security risks. A new wave of automated pen testing conducted through a software as a service delivery model can help reduce this risk by providing automated vulnerability findings in real time.