Privacy and Safety Guide for Users of X: Addressing Stalking Concerns
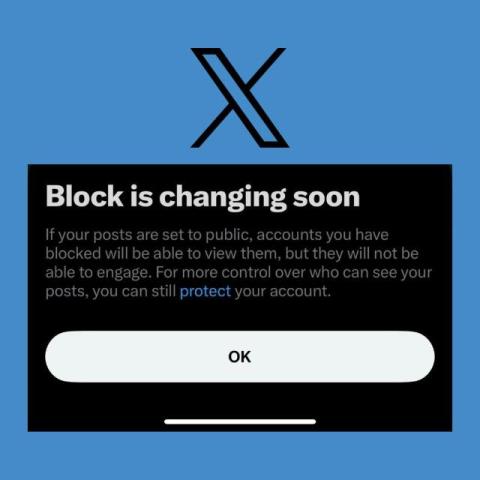
The recent updates to the blocking feature on X (formerly Twitter) have sparked significant concerns about user safety and privacy, particularly regarding stalking. These changes now permit blocked users to view posts but prevent them from engaging, such as liking, commenting, or sharing.