Security Benefits of Identity and Access Management (IAM)
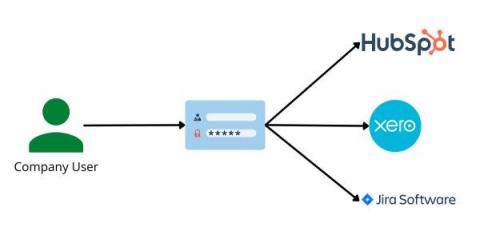
Identity and Access Management or Identity Access Management (IAM) is a critical security function for organizations of all sizes for privileged access management. By managing access to systems and data, IAM can help mitigate the risk of information breaches and protect the organization's most valuable assets through IAM technologies.