Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Access Management
Automation in Identity and Access Management and what it means for businesses
As organizations are looking to streamline processes and enhance security, pursuing automation in identity and access management is a key area businesses can target. By pursuing automation in identity and access management, IT teams can free up time to work on more important tasks, and reduce the friction required in managing team member and vendor access across necessary accounts, data and applications.
Role-based Access Control vs Attribute-based Access Control: Which to Choose
Industry-first research from Axis Security finds 65% percent of organizations plan to adopt a Security Service Edge platform within next two years
2023: The year of SASE? Not So Fast Says SSE!!!
If you’ve not downloaded the first ever SSE Adoption report conducted by CyberSecurity Insiders, do! CyberSecurity Insiders, is a 500,000+ member online community for information security professionals, bringing together the best minds dedicated to advancing cybersecurity and protecting organizations across all industries, company sizes, and security roles. They are a comprehensive source for everything related to cybersecurity – connecting people, opportunities, and ideas.
Top 6 Security Predictions for 2023
The pandemic created a huge shift in the workforce. Users got up from their desks, went home, and decided to stay there. As a result, users, devices, and data are now everywhere. This new way of working causes those of us in networking and security major challenges. The old castle and moat design no longer works and legacy security tools that worked in the past become ineffective in this new reality.
Key to success while implementing IAM- Best practices that every company should implement
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Identity and access management has emerged as an essential security element for organizations. A study reveals that 80% of global IT decision-makers have already adopted or are planning to adopt an IAM solution in the upcoming years.
The Rise of SSE-Powered Enterprises | 2023 SSE Adoption Report
Three easy steps to dramatically improve your AWS security posture: Step 1, set up IAM properly
Have you ever heard the saying that the greatest benefit of the cloud is that limitless resources can be spun-up with just a few clicks of the mouse? If so, you would be best served by forgetting that saying altogether. Just because cloud resources can be spun-up with a few clicks of the mouse does not mean that they should be. Rather, prior to launching anything in the cloud, careful consideration and planning are a necessity.
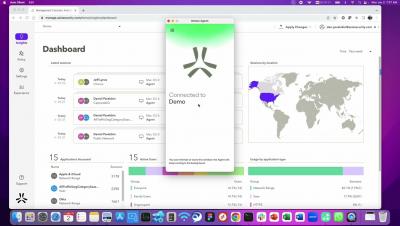
New Year, New Look, Axis 2023!
It's a new year and we are excited to share that the Atmos Agent has a new look! Learn more about Axis at https://www.axissecurity.com/