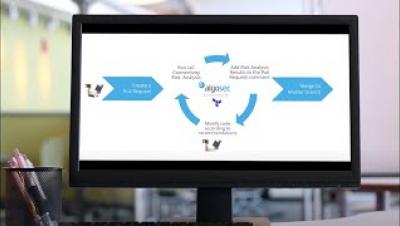
Webinar - Secure your IaC, infastrucutre as code best practices for security
The cloud revolution has taken the world, and programming languages, by storm! In 2022, HCL, the HashiCorp Configuration Language, driven by the popularity of Terraform and Infrastructure-as-Code practices, became the #1 fastest-growing language on GitHub! Who would’ve expected that ten years ago?!