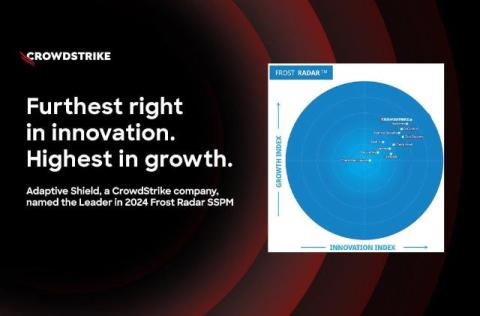
Adaptive Shield, a CrowdStrike Company, Leads in 2024 Frost Radar SSPM Leadership Report
CrowdStrike is proud to announce that Adaptive Shield is positioned as the leader in the Frost & Sullivan 2024 SaaS Security Posture Management (SSPM) Frost Radar, earning the highest and farthest-right position among all evaluated vendors. Adaptive Shield, which was acquired by CrowdStrike in November 2024, is recognized for its leadership in innovation and growth, with scores of 4.8/5 and 4.5/5, respectively, on the Frost Radar innovation index.