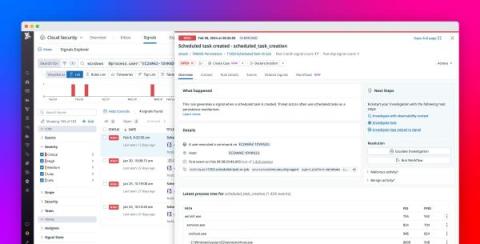
Lock pages in memory - and throw away the key
This Windows policy specifies which accounts can keep data in physical memory, preventing the system from paging it to virtual memory on disk. RAM (Random Access Memory) and virtual storage serve as two types of memory in a computer system, each with distinct functions and characteristics. RAM, the physical memory installed in a computer, provides fast access to actively used data by the CPU, determining the system’s multitasking capabilities.